[](/ebooks/cybersecurity-video-surveillance-systems/)
To offer solutions to some of the data security weaknesses common to traditional video surveillance systems, we’ve published a free eBook.
We’ve published the book’s contents here on our blog. The downloaded version includes a Vendor Selection Worksheet, an extra section that outlines key questions you should ask before purchasing a video security system for your business.
Download Your Copy HerePart 1: Surveillance System Design
Traditionally, closed-circuit television (CCTV) systems were exactly that — closed. Video cameras were wired to broadcast locally to a set number of monitors. The only way to breach the system was to gain physical access to the monitors while the broadcast was in progress.
We’ve come a long way—there now exist a number of approaches to enabling video surveillance of physical sites. The biggest change in recent years has been growing demand for remote access—the ability to manage security camera footage via connected devices such as laptops, tablets, smartphones.
To meet this new demand, security system providers have developed a number of different system designs. At a high-level, we describe these approaches as follows.
Traditional On-Prem + Internet Enabled Remote Access
Many of the world’s largest providers of security cameras and related equipment have adopted this system design to meet new demands of their connected clients. This approach retains the original system architecture — essentially video cameras plus a centralized, on-premise storage device — but adds an Internet connection to enable remote access.
Pros
- Works with your existing system architecture
- Available from established brands
Cons
- Difficult to keep up to date with the latest security patches and software
- Lots of configuration and manual updates required
- Requires complex VPN configuration and/or port forwarding to enable remote access
Video Surveillance as a Service (VSaaS)
Several years ago, a new group of providers entered the market to provide cloud-based storage and access. Generally speaking, VSaaS comes in two varieties:
Hosted video surveillance: Video is recorded, managed, and stored off site at the VSaaS provider’s data centre
Managed video surveillance: Video is recorded and stored at the customer’s site, but the provider manages it remotely
VSaaS providers typically do not manufacture their own hardware. Rather, they configure existing equipment to connect to their cloud-based services, which are typically powered by third-party storage and computing providers. While VSaaS providers often handle system management and upkeep, the systems themselves are not immune to the risks associated with outdated software and other vulnerabilities.
Pros
- Turn-key managed service
Cons
- Systems require provider to keep system updated and maintained; typically relies on manual updates
- If storage is hosted in the cloud, the system may hinder bandwidth
- Likely relies on VPN configuration and/or port forwarding to enable remote access
Cloud-Based Add-Ons
A third group of providers has developed physical adaptors that plug into DVRs and NVRs from established security equipment manufacturers. We describe these providers as “cloud-based add-ons,” given that they are designed to add capabilities to an existing system. Once connected, these devices enable functionality such as remote access, encoding of digital video, cloud storage and video analytics.
Pros
- Works with your existing system; don’t need to get rid of existing equipment
Cons
- May consume significant bandwidth because the system is constantly uploading footage to the cloud
- Often requires its own high-speed network to function properly, adding cost
- Updating software is not automatic—it typically requires intervention of the VSaaS provider to ensure success
- There are frequently interoperability challenges between components from different manufacturers
Tradeoffs: Information Security and Remote Access
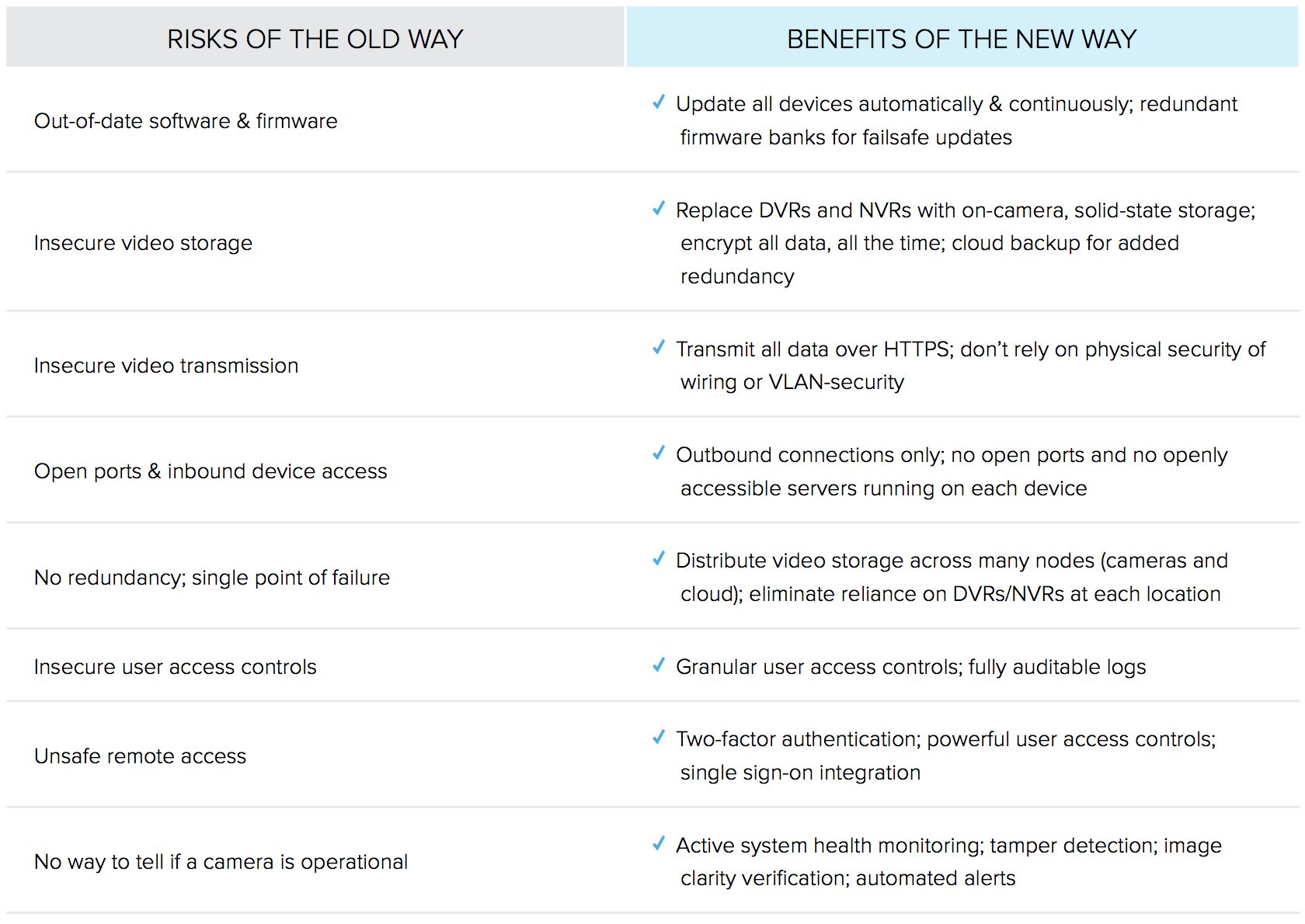
Historically, any video security system designed for businesses has presented a set of tradeoffs. Systems that rely on centralized on-premise storage — via NVRs or DVRs — typically face complexities when it comes to enabling remote access. These complexities are known to introduce vulnerabilities that may be exploited by malicious actors.
On the other hand, systems that rely purely on cloud-based storage remove the need for DVRs and NVRs, but this configuration comes at a cost: sending 100% of your recorded footage to the cloud can dramatically hinder the bandwidth of your local area network. Poorly designed cloud-based systems may also come with their own set of vulnerabilities.
The purpose of this white paper is not to dive deep into the details of each system type. Rather, we aim to highlight the most common software-related security shortcomings that arise from existing system designs. As with any investment for your business, it’s important to consult with your provider to fully understand the benefits and limitations of their proposed system design.
